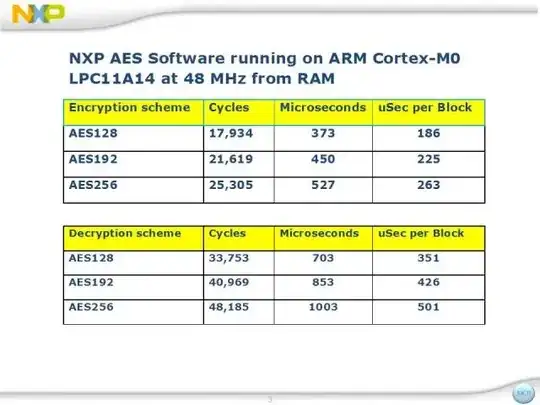
I have an embedded device. It produces larges files (200 MB). I want the device to encrypt the file before writing to disk, so I gave them all a 16-byte random key.
How can I transform the large file with the small key, with the least amount of CPU?
If I XOR the data with the 16byte key, its almost good enough. But it will show repeated patterns from which you can distract the key (for example if the input is 16 zeroes), but can I make it better without sacrificing on performance?