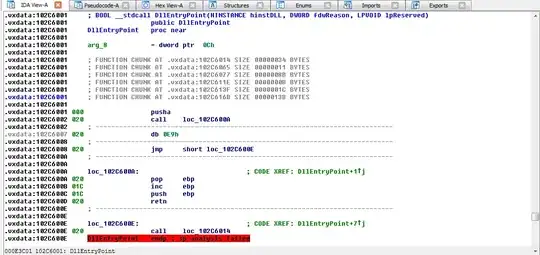
I am trying to reverse engineer a DLL file, but I am getting this warning when it's loaded:
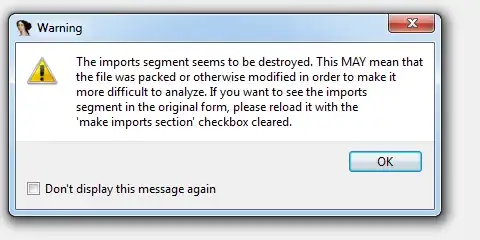
As well, then on some of the functions error appears sp analysis failed like on this picture:
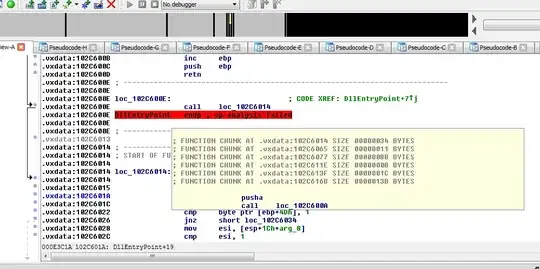
Is it possible to get code from that function ?
Once in pseudo code, there is only ";" inside the function. Parameters do match.