VM packers like Code Virtualizer and VMProtect seem challenging to existing reverse engineering work, especially static approach like IDA Pro.
According to this slides
www.hex-rays.com/products/ida/support/ppt/caro_obfuscation.ppt
from Hex-rays, IDA Pro requires experienced reverse engineer to manually recognize the opcode array and understand the semantic, then decode the bytecode array..
I myself use IDA Pro to deal with simple quicksort program using Code Virtualizer, and I can share two pics.
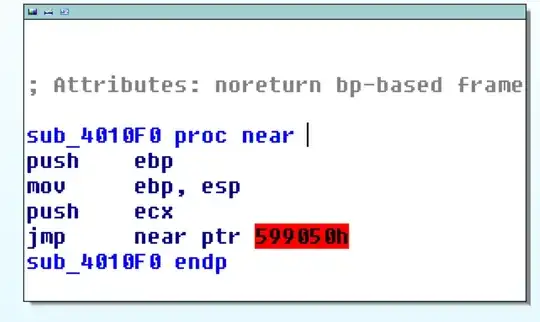
See, I use Code Virtualizer to protect this part and IDA Pro can not go to 0X599050h.
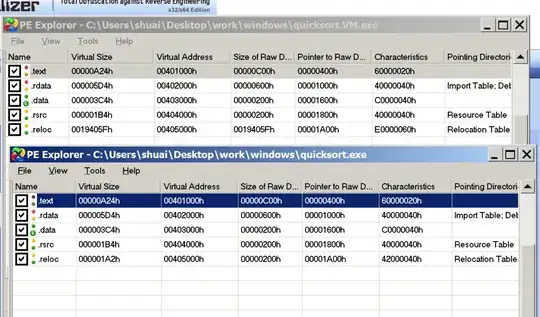
See, the size of relocation section has a significant growth.
So my questions:
- Can IDA Pro automatically deal with VM obfuscated binaries?
- Any other interesting materials on the state-of-art in this area?
Thank you!