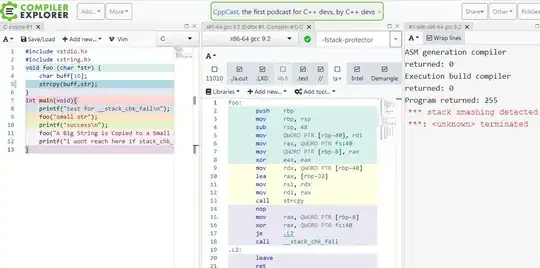
This is the part of the picoCTF 2019 problem "Investigative Reversing 0". I've encountered the following code when using Ghidra:
if (lVar1 != *(long *)(in_FS_OFFSET + 0x28)) {
/* WARNING: Subroutine does not return */
__stack_chk_fail();
}
Although I've completed the challenge using this as a guide: https://github.com/Dvd848/CTFs/blob/master/2019_picoCTF/Investigative_Reversing_0.md
I still don't understand this part of the code and what it does.After a few more detailed search I found two datatype assigned to the code:
long in_FS_OFFSET;
long lVar1;
I did research combining the code with ‘in_FS_OFFSET’ and ‘__stack_chk_fail()’ and most of them turned up as solution writeups on various CTF problems.Only a minority of them are something else.Such as this: https://hackaday.io/project/164346-andxor-dc27-badge/log/164366-reverse-engineering-with-ghidra-simtaco-floppy-challenge
The site have very similar de-compiled results, so I'm thinking this part of the code had something to do in protecting the program from stack-overflow.I looked at the source code of the program in the bottom of the site and searched all the c library included, but I found no useful hints. I returned to Ghidra and found this undefined function:
void UndefinedFunction_00101036(void)
{
/* WARNING: Treating indirect jump as call */
(*(code *)(undefined *)0x0)();
return;
}
Does this undefined function have anything to do with my question? If so, what might be the original code be? Thanks in advance for any answers.
Edit: disassembly part of the code
00101380 64 48 33 XOR sVar2,qword ptr FS:[0x28]
04 25 28
00 00 00
00101389 74 05 JZ LAB_00101390
0010138b e8 d0 fc CALL __stack_chk_fail undefined __stack_chk_fail()
ff ff
-- Flow Override: CALL_RETURN (CALL_TERMINATOR)
and the function:
//
// .plt
// SHT_PROGBITS [0x1020 - 0x109f]
// ram: 00101020-0010109f
//
LAB_00101020 XREF[9]: 0010103b(j), 0010104b(j),
0010105b(j), 0010106b(j),
0010107b(j), 0010108b(j),
0010109b(j), 001020b4,
_elfSectionHeaders::00000310(*)
00101020 ff 35 6a PUSH qword ptr [PTR_00103f90] = 00000000
2f 00 00
00101026 ff 25 6c JMP qword ptr [PTR_00103f98]
2f 00 00