recently i got my hands on one sample that self-modifies its .text section. So, I placed a breakpoint on .text section on write operation and then continued. I found out that it zeroes out the .text section and then writes the decrypted code to that section and then makes a call to the decrypted OEP. I used Scylla to correct the OEP and dump the .exe file.
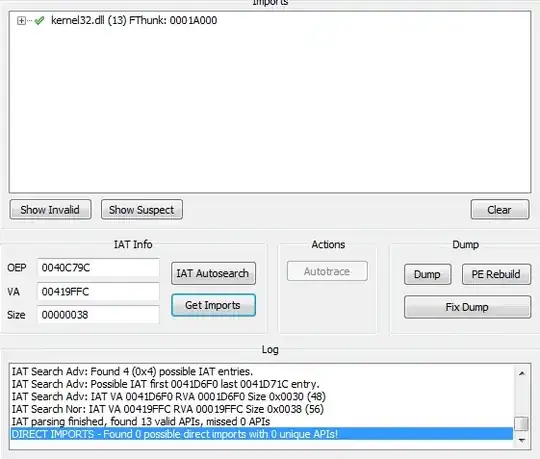
When i get the imports it shows that the program only imports kernel32.dll.
This is the assembly of the dumped .exe file in the PEBear.
This is what I get when i try to open the dumped file in ImmunityDbg.
The imports i get are also very different from what Scylla gave me + The dumped program does not run it crashes right away. What am i doing wrong?
Thanks.


9ed85a6de31604eb431cdd7632cad0e5be54af10a16cc6ca0b886d1f92bb91b8– rustam Shirinov Oct 23 '17 at 10:31IsDebuggerPresentbut i already patched it. – rustam Shirinov Oct 23 '17 at 17:46