 I'm learning about Feistel Ciphers at the moment, but having issues with the formulae, so I can't move on from it.
I'm learning about Feistel Ciphers at the moment, but having issues with the formulae, so I can't move on from it.
Encryption:
- $_{+1} = _$
- $_{+1} = _ \oplus ( _ , _)$
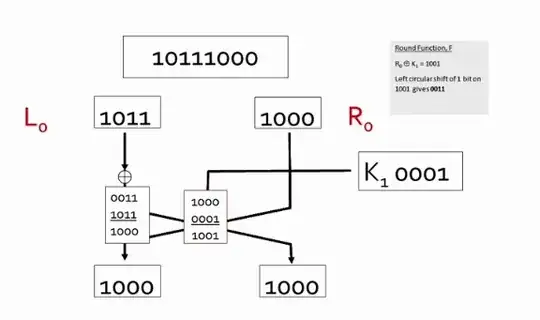
For the round function $( _ , _)$, could someone advise on what exactly I need to do? Let's say my key is $1197$, what needs to happen in between the brackets, $(_ , _)$ , full diagram screenshot attached, thanks.