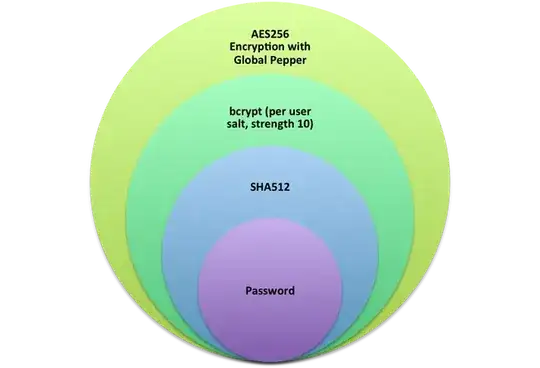
I understand that the Global "pepper" means that a DB dump protects the hashes until that pepper is found, and then each hash is still salted per user, but how much would that slow down people reversing the passwords in the event of a DB leak over simply bcrypting them ?
If you use AES with a random 128-bit key (the smallest key size), an attacker who obtains the encrypted hashes but not the key is effectively dead on their tracks. Carrying a brute force attack against AES is impossible in practice.
Is this really more secure than using bcrypt with a complexity of 11 or 12 ? The password "chain" is secure as its weakest part, so is there any point adding the extra 2 parts in ?
Instead of asking "is it more secure" in general terms as you do, we need to actually be specific and ask:
- Are there any scenarios that it protects against that just bcrypt doesn't?
- Are those scenarios likely enough risks that it's worth the additional complexity?
The use of an additional encryption step, in particular, protects against scenarios where the attacker manages to acquire the encrypted scrambled passwords but not the encryption key. If the attacker acquires both, then it doesn't do anything.
So it only provides additional security in scenarios where the defender can successfully arrange for that condition to be met. There are some plausible scenarios that meet that description:
- An attacker acquires the encrypted password hashes by executing a SQL injection or similar attack against a front-end web application, but the encryption key is not stored in the RDBMs where the entries are.
- The attacker gains access to a host that has all of the password entries, but no such host ever contains the encryption key.
The latter scenario can be arranged by having a Hardware Security Module or a special, hardened server (e.g., the Transit backend in Hashicorp's Vault) be the sole owner of the encryption keys, so that the other servers that possess the password database can only ever encrypt or decrypt password entries by sending the ciphertexts over to that specialized key owner to do it for them. But that requires extra cost and effort to acquire, develop, harden and/or configure; and it becomes an extra point of failure that is capable of bringing the whole system down.
So is it worth the extra effort and complexity? That's a judgment call.