In a 128-bits Feistel Cipher:
I need suggestions about two variations of the Round Function
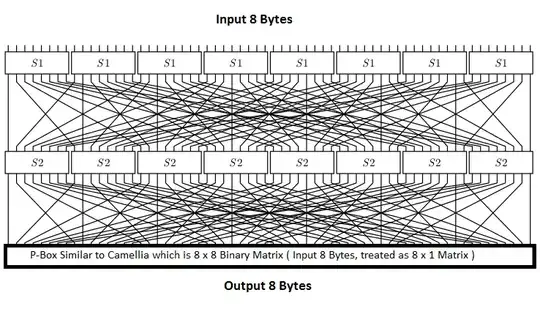
Variation-1
- $64$ bit input is divided into $8$ bytes
- Byte $0,1,2,3$ are substituted with Sbox1
- Byte $4,5,6,7$ are substituted with Sbox2.
- Then a $8 \times 8$ Binary Matrix is applied on the 8 bytes from 8 rows (Matrix similar to Camellia).
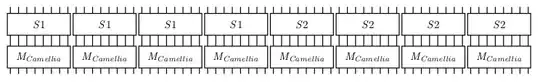
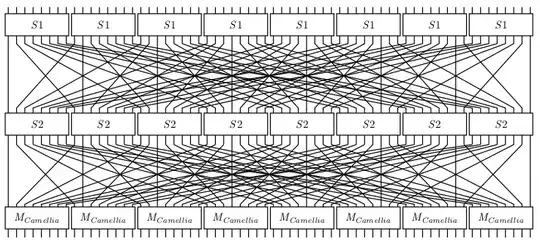
Variation-2
- 64 bit input of the round function is expressed as $8 \times 8$ binary matrix.
- Sbox1 is applied on the rows (on 8 bytes).
- Sbox2 is applied on the columns (on 8 bytes).
- 8 Bytes are made using bits of Rows.
- Then a $8 \times 8$ Binary Matrix is applied on the 8 bytes from 8 rows (Matrix similar to Camellia).
Keeping in view that both S-boxes have non-linearity of 112 and maximum Differential Probability of $2^{-6}$ ($\approx$ the same level of security of AES).
Which variation is better in terms of security ? The same S-boxes are used in both the variations. Variation-2 is slow and more complex to implement, but thats not a issue