I have 2 different images, one original, and one locked by a malware detected by eset as "Win32/Filecoder.Q".
How to detect the encryption method that is used and the key, that is not using any public key/rsa/rc4 algorithm. There is diff:
If needed I can attached files (locked and original).

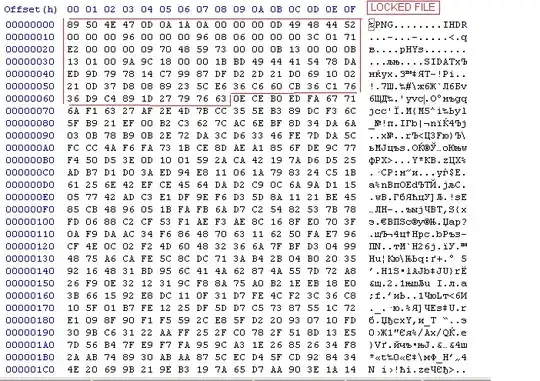
yvcand.O°for the locked file? – Apr 24 '16 at 06:24