I'm wondering why hash constructions aren't parallel like CTR mode for encryption?
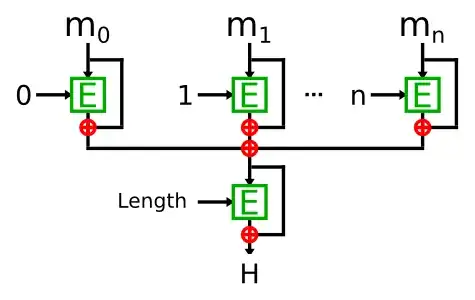
For example: We have ideal block cipher E, where we encrypt message block with counter and xor output block with message block. Then we xor (sum) all blocks and encrypt it with length of message and xor with sum of all blocks to get hash. If last message block is shorter than block size it is padded with zeroes.
$H_{0} = E_{0}(m_{0}) \oplus m_{0}$
$H_{1} = E_{1}(m_{1}) \oplus m_{1}$
$...$
$H_{n} = E_{n}(m_{n}) \oplus m_{n}$
$H_{sum} = H_{0} \oplus H_{1} \oplus ...\oplus H_{n}$
$H = E_{Length}(H_{sum}) \oplus H_{sum}$
Is such construction known to be insecure? Or is it secure?