Let's say I have fileA and fileB, both encrypted somehow, but in the same method with different keys.
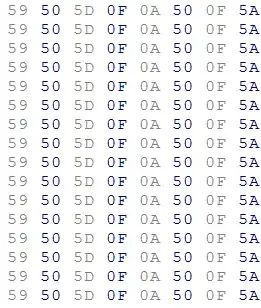
If I xor them together, they will make a repeating pattern of 32 bytes length.
What does that say about the repeating pattern, the encryption pattern, and the likelihood of the unencrypted files to be identical?
Is there any way to extract the keys used to encrypt them?
Is there a way, other than to open up Ollydbg and try to reverse engineer the decryption procedure?
The program contacts a server, sends a certain unique code, and the server replies back with an md5 hash. Then the server sends back the encrypted file, which is easily decrypted by the program. I want to reverse engineer this program and encryption method.
This is not a homework question, this is a real situation that is tormenting me.
The decrypted plaintext is either Lua source or Lua VM bytecode, with a small possibility of being XML.
Edit: I now realize that the repeating sequence is probably two different MD5 hashes XOR'd with each other. Is there a method to analyze and try to extract the individual MD5 hashes?
Analyzing / decrypting a block of datafor a question that doesn't contain an explicit request to do so isn't a valid close reason. – rath Apr 19 '14 at 05:55