The handling of keys is known as key management. The establishment of the same symmetric or secret key between two or more parties is called key establishment.
Symmetric keys should be kept secret from other parties than the participants in the scheme. The term "secret key" is often used as a synonym for the symmetric key. The private keys for asymmetric schemes are not shared, but are of course also kept secret, as privacy implies secrecy.
The establishment of symmetric keys between parties can be performed in several ways:
Key Agreement (KA): the establishment of a key using a key agreement scheme such as DH or ECDH - usually followed by a KDF (see below);
Key Encapsulation (KE) or Key Wrapping (KW): the sending of a key encrypted by another (public) key;
Key Sharing schemes: the creation of a key from key parts held by different persons;
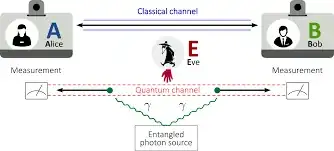
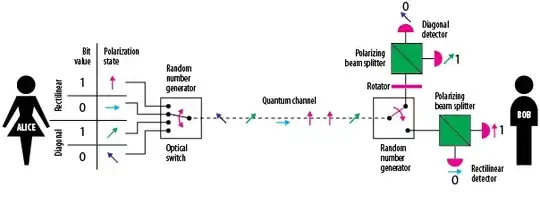
Quantum Key Distribution (QKD), the distribution of keying material over an optically linked connection that is impossible to eavesdrop.
Out-of-band" procedures: the transport of a randomly generated key using, for instance: a previous telephone call, a letter or the handover of a data carrier like a USB thumbdrive.
It is possible to derive new key material from a pre-shared secret as well. In that case we are talking about derivation from a base key using a Key Derivation Function (KDF). A KDF commonly uses the some kind of input keying material usually a master key or base key. The derived keys are often also dependent using other data as input such as a salt or a output-key specific label.
If the derivation is performed so the resulting keys can be used in different schemes it is often called key diversification. If the key is generated from a password we talk about a Password Based KDF or PBKFD, sometimes also used as a "password hash". If keys are derived in by advancing some kind of state or by relying on past keys we talk about a key ratchet.
There are other methods for establishing symmetric keys, but these are some of the most commonly used ones. The security of these schemes depends - of course - not just on the method but also on the implementation.