You can get access to this document via institutional login at https://www.researchgate.net/publication/220556089_Security_and_composition_of_cryptographic_protocols_A_tutorial So in Ran Canettis Tutorial on Composable Security I came across some definitions of how protocols can be composed:
Earlier, it explains an example on what can go wrong if protocols are composed. He mentioned an example, where you use a key-exchange protocol and One-Time-Pad encryption. Each protocol itself is secure, but the composed one is obviously not secure.

Much later he states a theorem:
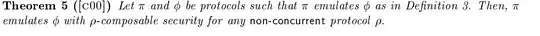
Now my question is, isn't the example earlier a non-concurrent composition? A simple nested protocol, where we first do key-exchange, then do the encryption, and now are ready for oracle requests again in the key-exchange? That would be a counter-example for this theorem, that such a protocol is not secure. My problem is understanding concurrent vs non-concurrent composition. I thought concurrent is executing the protocols "at the same time". You try to use information in one execution in another one, and else wise it is non-concurrent.

