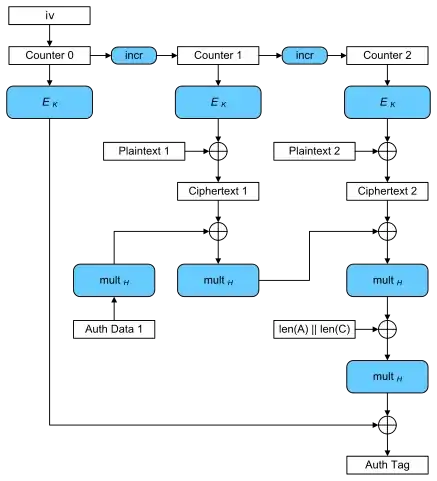
Say, for an AES-GCM encryption, an attacker knows essentially everything except the key. This would include:
- Plaintext
- Ciphertext
- IV
- Algorithm (AES-GCM)
In this case, will the attacker gain any advantage towards learning the key?
The application: I am using Password-Based Encryption following PKCS #5 recommendations. When the user supplies a password, I want the application code to know that the password provided was correct or incorrect. To accomplish this, I propose decrypting an IV+ciphertext with the key derived from the user-supplied password. If the decrypted data matches the expected plaintext value, then I know the user-supplied password provided is correct. And conversely, if it doesn't match, then user-supplied password is incorrect.