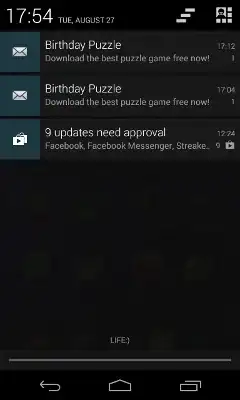
I noticed when I start an app, often an Heyzap interstitial ad appears (I had the Heyzap app but removed it 2 days ago).
Today I ran my own app that I've compiled from the Android SDK that definitely does not have any Heyzap code, but still, the banner appeared.
I think the problem arrived after installing "Lost Temple Jump" game from Google Play. It was asking for permission to push notifications. I said No.
My device is not rooted, is it possible that these games root my device and started to insert Heyzap banner to every other app ?
Screenshots:


Running processes list:
USER PID PPID VSIZE RSS WCHAN PC NAME
root 1 0 556 424 ffffffff 00000000 S /init
root 2 0 0 0 ffffffff 00000000 S kthreadd
root 3 2 0 0 ffffffff 00000000 S ksoftirqd/0
root 6 2 0 0 ffffffff 00000000 S migration/0
root 16 2 0 0 ffffffff 00000000 S khelper
root 17 2 0 0 ffffffff 00000000 S suspend_sys_syn
root 18 2 0 0 ffffffff 00000000 S suspend
root 20 2 0 0 ffffffff 00000000 S irq/203-msmdata
root 21 2 0 0 ffffffff 00000000 S sync_supers
root 22 2 0 0 ffffffff 00000000 S bdi-default
root 23 2 0 0 ffffffff 00000000 S kblockd
root 24 2 0 0 ffffffff 00000000 S msm_slim_ctrl_r
root 25 2 0 0 ffffffff 00000000 S khubd
root 26 2 0 0 ffffffff 00000000 S irq/84-msm_iomm
root 27 2 0 0 ffffffff 00000000 S irq/84-msm_iomm
root 28 2 0 0 ffffffff 00000000 S irq/96-msm_iomm
root 29 2 0 0 ffffffff 00000000 S irq/96-msm_iomm
root 30 2 0 0 ffffffff 00000000 S irq/94-msm_iomm
root 31 2 0 0 ffffffff 00000000 S irq/94-msm_iomm
root 32 2 0 0 ffffffff 00000000 S irq/92-msm_iomm
root 33 2 0 0 ffffffff 00000000 S irq/92-msm_iomm
root 34 2 0 0 ffffffff 00000000 S irq/100-msm_iom
root 35 2 0 0 ffffffff 00000000 S irq/100-msm_iom
root 36 2 0 0 ffffffff 00000000 S irq/86-msm_iomm
root 37 2 0 0 ffffffff 00000000 S irq/86-msm_iomm
root 38 2 0 0 ffffffff 00000000 S irq/90-msm_iomm
root 39 2 0 0 ffffffff 00000000 S irq/90-msm_iomm
root 40 2 0 0 ffffffff 00000000 S irq/88-msm_iomm
root 41 2 0 0 ffffffff 00000000 S irq/102-msm_iom
root 42 2 0 0 ffffffff 00000000 S irq/102-msm_iom
root 43 2 0 0 ffffffff 00000000 S irq/98-msm_iomm
root 44 2 0 0 ffffffff 00000000 S irq/98-msm_iomm
root 45 2 0 0 ffffffff 00000000 S irq/243-msm_iom
root 46 2 0 0 ffffffff 00000000 S irq/243-msm_iom
root 47 2 0 0 ffffffff 00000000 S irq/269-msm_iom
root 48 2 0 0 ffffffff 00000000 S irq/269-msm_iom
root 49 2 0 0 ffffffff 00000000 S l2cap
root 50 2 0 0 ffffffff 00000000 S a2mp
root 51 2 0 0 ffffffff 00000000 S cfg80211
root 52 2 0 0 ffffffff 00000000 S irq/644-earjack
root 53 2 0 0 ffffffff 00000000 S modem_notifier
root 54 2 0 0 ffffffff 00000000 S smd_channel_clo
root 55 2 0 0 ffffffff 00000000 S smsm_cb_wq
root 57 2 0 0 ffffffff 00000000 S qmi
root 58 2 0 0 ffffffff 00000000 S nmea
root 59 2 0 0 ffffffff 00000000 S msm_ipc_router
root 60 2 0 0 ffffffff 00000000 S apr_driver
root 61 2 0 0 ffffffff 00000000 S irq/337-mdm sta
root 62 2 0 0 ffffffff 00000000 S irq/334-mdm pbl
root 64 2 0 0 ffffffff 00000000 S kswapd0
root 65 2 0 0 ffffffff 00000000 S fsnotify_mark
root 66 2 0 0 ffffffff 00000000 S cifsiod
root 67 2 0 0 ffffffff 00000000 S crypto
root 81 2 0 0 ffffffff 00000000 S mdp_dma_wq
root 82 2 0 0 ffffffff 00000000 S mdp_vsync_wq
root 83 2 0 0 ffffffff 00000000 S mdp_pipe_ctrl_w
root 84 2 0 0 ffffffff 00000000 S mdp_cursor_ctrl
root 85 2 0 0 ffffffff 00000000 S hdmi_hdcp
root 86 2 0 0 ffffffff 00000000 S irq/111-hdmi_ms
root 87 2 0 0 ffffffff 00000000 S dtv_work
root 88 2 0 0 ffffffff 00000000 S vidc_worker_que
root 89 2 0 0 ffffffff 00000000 S vidc_timer_wq
root 90 2 0 0 ffffffff 00000000 S smux_notify_wq
root 91 2 0 0 ffffffff 00000000 S smux_tx_wq
root 92 2 0 0 ffffffff 00000000 S smux_rx_wq
root 93 2 0 0 ffffffff 00000000 S smux_loopback_w
root 94 2 0 0 ffffffff 00000000 S diag_wq
root 95 2 0 0 ffffffff 00000000 S hsic_diag_wq
root 96 2 0 0 ffffffff 00000000 S hsic_2_diag_wq
root 97 2 0 0 ffffffff 00000000 S smux_diag_wq
root 98 2 0 0 ffffffff 00000000 S diag_cntl_wq
root 99 2 0 0 ffffffff 00000000 S diag_dci_wq
root 100 2 0 0 ffffffff 00000000 S kgsl-3d0
root 101 2 0 0 ffffffff 00000000 S anx7808_work
root 102 2 0 0 ffffffff 00000000 S irq/645-anx7808
root 104 2 0 0 ffffffff 00000000 S irq/330-wcd9xxx
root 109 2 0 0 ffffffff 00000000 S usbnet
root 112 2 0 0 ffffffff 00000000 S mdm_bridge
root 113 2 0 0 ffffffff 00000000 S ks_bridge:1
root 114 2 0 0 ffffffff 00000000 S ks_bridge:2
root 115 2 0 0 ffffffff 00000000 S ks_bridge:3
root 116 2 0 0 ffffffff 00000000 S ks_bridge:4
root 117 2 0 0 ffffffff 00000000 S k_rmnet_mux_wor
root 118 2 0 0 ffffffff 00000000 S f_mtp
root 119 2 0 0 ffffffff 00000000 S file-storage
root 120 2 0 0 ffffffff 00000000 S uether
root 121 2 0 0 ffffffff 00000000 S touch_wq
root 123 2 0 0 ffffffff 00000000 S iewq
root 124 2 0 0 ffffffff 00000000 S kinteractiveup
root 125 2 0 0 ffffffff 00000000 S binder
root 126 2 0 0 ffffffff 00000000 S mmcqd/0
root 130 2 0 0 ffffffff 00000000 S krfcommd
root 131 2 0 0 ffffffff 00000000 S rq_stats
root 132 2 0 0 ffffffff 00000000 S deferwq
root 135 2 0 0 ffffffff 00000000 S vibrator
root 136 2 0 0 ffffffff 00000000 S fsa8008
root 137 2 0 0 ffffffff 00000000 S irq/369-fsa8008
root 138 2 0 0 ffffffff 00000000 S irq/371-fsa8008
root 139 1 476 312 ffffffff 00000000 S /sbin/ueventd
root 141 2 0 0 ffffffff 00000000 S jbd2/mmcblk0p21
root 142 2 0 0 ffffffff 00000000 S ext4-dio-unwrit
root 147 2 0 0 ffffffff 00000000 S jbd2/mmcblk0p22
root 148 2 0 0 ffffffff 00000000 S ext4-dio-unwrit
root 152 2 0 0 ffffffff 00000000 S jbd2/mmcblk0p23
root 153 2 0 0 ffffffff 00000000 S ext4-dio-unwrit
root 154 2 0 0 ffffffff 00000000 S jbd2/mmcblk0p20
root 155 2 0 0 ffffffff 00000000 S ext4-dio-unwrit
system 165 1 884 340 ffffffff 00000000 S /system/bin/servicemanager
root 166 1 4008 664 ffffffff 00000000 S /system/bin/vold
system 167 1 1084 456 ffffffff 00000000 S /system/bin/qcks
root 168 1 10868 1696 ffffffff 00000000 S /system/bin/netd
root 169 1 976 576 ffffffff 00000000 S /system/bin/debuggerd
radio 170 1 14416 2848 ffffffff 00000000 S /system/bin/rild
system 171 1 96384 8688 ffffffff 00000000 S /system/bin/surfaceflinger
root 172 1 827808 39576 ffffffff 00000000 S zygote
drm 173 1 13308 3476 ffffffff 00000000 S /system/bin/drmserver
media 174 1 48868 8648 ffffffff 00000000 S /system/bin/mediaserver
install 175 1 896 492 ffffffff 00000000 S /system/bin/installd
keystore 177 1 3248 1052 ffffffff 00000000 S /system/bin/keystore
nobody 178 1 2144 548 ffffffff 00000000 S /system/bin/rmt_storage
radio 179 1 6320 640 ffffffff 00000000 S /system/bin/bridgemgrd
radio 180 1 7388 440 ffffffff 00000000 S /system/bin/qmuxd
radio 181 1 7580 700 ffffffff 00000000 S /system/bin/netmgrd
root 182 1 20848 828 ffffffff 00000000 S /system/bin/thermald
root 183 1 6200 472 ffffffff 00000000 S /system/bin/mpdecision
root 189 2 0 0 ffffffff 00000000 S hsicctl0
root 190 2 0 0 ffffffff 00000000 S hsicctl1
root 191 2 0 0 ffffffff 00000000 S hsicctl2
root 192 2 0 0 ffffffff 00000000 S hsicctl3
nobody 193 1 10444 668 ffffffff 00000000 S /system/bin/sensors.qcom
media_rw 194 1 2708 988 ffffffff 00000000 S /system/bin/sdcard
camera 195 1 4976 2472 ffffffff 00000000 S /system/bin/mm-qcamera-daemon
system 197 1 2132 324 ffffffff 00000000 S /system/bin/qseecomd
shell 198 1 4544 280 ffffffff 00000000 S /sbin/adbd
system 244 197 4232 432 ffffffff 00000000 S /system/bin/qseecomd
system 553 172 1016800 92148 ffffffff 00000000 S system_server
system 575 167 1064 476 ffffffff 00000000 S /system/bin/efsks
root 577 2 0 0 ffffffff 00000000 S ehci_wq
root 578 2 0 0 ffffffff 00000000 S irq/337-hsic_pe
system 586 575 2892 2108 ffffffff 00000000 S /system/bin/ks
root 873 2 0 0 ffffffff 00000000 S WD_Thread
root 874 2 0 0 ffffffff 00000000 S MC_Thread
root 875 2 0 0 ffffffff 00000000 S TX_Thread
root 876 2 0 0 ffffffff 00000000 S RX_Thread
wifi 912 1 3196 1824 ffffffff 00000000 S /system/bin/wpa_supplicant
u0_a57 966 172 906368 78664 ffffffff 00000000 S com.android.systemui
u0_a49 1063 172 867320 33476 ffffffff 00000000 S com.android.phasebeam
u0_a34 1078 172 888692 58356 ffffffff 00000000 S com.google.android.inputmethod.latin
u0_a23 1094 172 1008768 48316 ffffffff 00000000 S com.google.process.location
radio 1111 172 890824 48388 ffffffff 00000000 S com.android.phone
nfc 1134 172 858504 27604 ffffffff 00000000 S com.android.nfc
u0_a35 1148 172 941812 83760 ffffffff 00000000 S com.android.launcher
nfc 1191 172 838592 22292 ffffffff 00000000 S com.android.nfc:handover
u0_a23 1206 172 894992 38360 ffffffff 00000000 S com.google.process.gapps
u0_a23 2408 172 853692 30292 ffffffff 00000000 S com.google.android.gsf.login
root 2882 2 0 0 ffffffff 00000000 S msm_sat0
u0_a52 3224 172 871816 43784 ffffffff 00000000 S com.google.android.apps.plus
root 4232 2 0 0 ffffffff 00000000 S flush-179:0
u0_a15 10631 172 841044 27908 ffffffff 00000000 S android.process.media
u0_a0 11406 172 873656 33396 ffffffff 00000000 S android.process.acore
root 11868 2 0 0 ffffffff 00000000 S msm_sat1
u0_a41 12007 172 907300 44000 ffffffff 00000000 S com.android.mms
u0_a85 12022 172 883760 46120 ffffffff 00000000 S com.facebook.katana
u0_a10 14365 172 1143480 119444 ffffffff 00000000 S com.android.chrome
u0_i3 14790 172 978188 107236 ffffffff 00000000 S com.android.chrome:sandboxed_process3
u0_a20 15454 172 882408 50200 ffffffff 00000000 S com.google.android.gallery3d
u0_i6 15558 172 959980 92904 ffffffff 00000000 S com.android.chrome:sandboxed_process1
u0_i8 15882 172 975888 110908 ffffffff 00000000 S com.android.chrome:sandboxed_process0
u0_a60 16597 172 909308 48052 ffffffff 00000000 S com.google.android.googlequicksearchbox
u0_a86 19209 172 892496 66084 ffffffff 00000000 S com.vkontakte.android
u0_a77 21519 172 874672 49400 ffffffff 00000000 S com.android.dialer
root 23312 2 0 0 ffffffff 00000000 S kworker/0:1
root 23483 2 0 0 ffffffff 00000000 S kworker/0:4
dhcp 23515 1 916 456 ffffffff 00000000 S /system/bin/dhcpcd
root 24028 2 0 0 ffffffff 00000000 S kworker/0:0
root 24246 2 0 0 ffffffff 00000000 S kworker/u:5
root 24257 2 0 0 ffffffff 00000000 S kworker/u:16
root 24260 2 0 0 ffffffff 00000000 S kworker/u:19
root 24268 2 0 0 ffffffff 00000000 S kworker/u:27
root 24276 2 0 0 ffffffff 00000000 S kworker/u:37
root 25927 2 0 0 ffffffff 00000000 S kworker/0:3
u0_a114 27884 172 877056 47332 ffffffff 00000000 S com.facebook.orca
u0_a84 28165 172 923156 83408 ffffffff 00000000 S com.skype.raider
u0_a50 29850 172 924516 78784 ffffffff 00000000 S com.android.vending
u0_a98 30061 172 859416 30808 ffffffff 00000000 S com.whatsapp
root 30273 2 0 0 ffffffff 00000000 S kworker/0:2
u0_a13 30482 172 835224 22172 ffffffff 00000000 S com.android.defcontainer
u0_a27 30513 172 835468 22516 ffffffff 00000000 S com.google.android.partnersetup
u0_a43 30533 172 835268 21956 ffffffff 00000000 S com.android.musicfx
u0_a23 30553 172 951380 33212 ffffffff 00000000 S com.google.android.gms
u0_a105 30580 172 839056 26348 ffffffff 00000000 S com.potyomkin.talkingkote
u0_a144 30599 172 871284 38764 ffffffff 00000000 S net.mobilecraft.football
u0_a145 30622 172 840464 25272 ffffffff 00000000 S net.mobilecraft.realbasketball
system 30816 172 842864 25720 ffffffff 00000000 S com.android.settings
u0_a40 30887 172 838084 24220 ffffffff 00000000 S com.google.android.apps.uploader
u0_a67 30904 172 866464 30244 ffffffff 00000000 S com.google.android.youtube
u0_a7 31082 172 836036 24164 ffffffff 00000000 S com.android.providers.calendar
u0_a6 31096 172 844188 24432 ffffffff 00000000 S com.google.android.calendar
u0_a140 31168 172 837860 23104 ffffffff 00000000 S com.gismeteo.client
shell 31203 198 1132 468 00000000 b6e88040 R ps
u0_a96 31346 172 904276 102608 ffffffff 00000000 S com.topface.topface