Seems that Android 13 doesn't allow any more access to /system/bin/ip command.
I tried to list the connected hotspot devices via ip neigh [1].
The error message is:
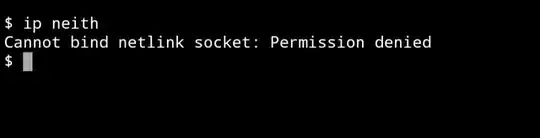
Cannot bind netlink socket: Permission denied
Is there any way to fix that issue in Android 13?
So far I tried it with the following terminal apps
- Temux
v0.101v0.118.0 (via F-Droid) - Terminal Emulator for Android v1.0.70
ipcommand without flags return anything? (the screenshot shows a typoneith, which would showObject "neith" is unknown, try "ip help"on Android 12) – Andrew T. Sep 08 '22 at 09:38ipreturns, that it is not installed, and I can do that viaiproute2ortermux-toolspackage. I'll try that now... – wittich Sep 08 '22 at 09:41/data/data/com.termux/files/usr/bin/ipcomes with the same error:Cannot bind netlink socket: Permission denied. – wittich Sep 08 '22 at 09:44iproute2packageman ipand the search forip neighsays:Shows the current neighbour table in kernel. – wittich Sep 08 '22 at 09:49