I recently wanted to install a metronome app, so I downloaded one from the Play Store, but in the "install" step nothing happened. The app just wasn't there. I installed another one and forgot about that strange issue.
Yesterday though, something started to happen. Every now and then (and it's getting more and more frequently), I get a notification that some app tried to install itself (!) but was blocked because it's from "unknown sources", and it's prompting me to disable the "block install from unknown sources" check from Settings.
It looks like there are more than one apps trying to install themselves: "Superb Cleaner". "com.android.helper.patch[...]" and some more.
At first I though these might be system updates and was tempted to disable the "unknown source" block, but now I am worried I might have some malware on my phone.
I do have some sensitive information (browser logins, credit card data), and I also don't want to factory reset my phone.
Where should I search for the APK that is trying to install itself (or the APKs)?
EDIT: It's this application: https://play.google.com/store/apps/details?id=com.andymstone.metronome. I'm not entire sure the app is the cause, but it's strange that I don't have it installed, but in my google play account it appears as "Installed"...
My phone is an Allview X2 Soul Style with Android 5.1.
After I have unchecked the "block apps from unknown sources", now I keep getting prompted the install screen for these apps. I keep pressing "Cancel" but they come again every half an hour or so. :(
EDIT2: Here are the adb logs requested: Windows and Activities
EDIT3: Dumpsys log for the suspicious package: Dumpsys

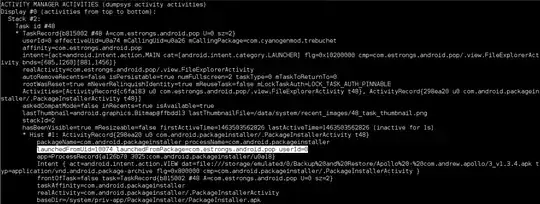
adb shell dumpsys window windowsand/oradb shell dumpsys activity activitiesand provide us the output? The output may be large (overwhelming), so use a code paste service, such as pastebin to upload it. Do provide us the screenshot for that installation prompt. – Firelord Apr 29 '16 at 15:39com.android.tools.callassistantis reported as malware by AVG and so as at many places on web per Google search. Seems to go by the label Caller ID. // Bogdan: could you doadb uninstall com.android.tools.callassistantand later see ifadb shell pm list packages com.android.tools.callassistantreports anything? – Firelord May 05 '16 at 13:53adb shell dumpsys package com.android.tools.callassistant? After that, doadb shell pm hide com.android.tools.callassistant. – Firelord May 05 '16 at 15:26pm hidemakes Android treat the relevant package as being uninstalled, which means it wouldn't run at all unless it is reinstated.pm disableis more flexible and requires higher privileges but in the end, our goal to disable the package has been achieved. As for the prompts, if they are like this then my answer here might be of some service to you. – Firelord May 09 '16 at 16:52